Phishing attacks result in significant losses and damages to businesses every year
For Google and Facebook, the losses totaled more than $100 million. Belgium’s Creland Bank handed over more than $75 million to cybercriminals. And the Austrian aerospace parts maker FACC lost $61 million. What’s causing these types of massive losses? Each of these organizations were the victims of different (and costly) types of phishing attacks.
What’s a phishing attack?
In general, a phishing scam is a type of cyberattack that cybercriminals use to get users to perform some type of action. These emails are often sent out in mass with the goal of tricking unsuspecting individuals into falling for their scam. Think of your best bud — the Nigerian Prince who keeps trying to get you to take his money for “safe keeping.”
However, phishing has evolved significantly since his royal highness first entered the scene. There is now a variety of phishing attacks targeting businesses each day. Some involve the use of emails and websites; others may use text messages or even phone calls. Attacks use these methods with the goal of getting users to provide personal or account information or to make wire transfer funds to fraudulent accounts. The cybercrime industry is reaching unprecedented levels. Cybersecurity Ventures reports that the damages of cybercrime are expected to cost the world $6 trillion annually by 2021 — of which phishing is anticipated to play a significant role.
But when we talk about phishing, what types of phishing attacks are we specifically talking about? There are actually multiple types of phishing scams that businesses are targeted by on a daily basis.
Let’s hash it out.
10 types of phishing attacks that can snare your business
As you can probably tell from reading our blog posts, we like lists. A lot. In this case, we’ve put together a list of the most prevalent types of phishing attacks. The goal here is to help familiarize you with many of the different types of phishing attacks that exist and provide an overview of how they work or what sets them apart from other phishing scams.
Just note that we have them in alphabetical order and not in any particular order of importance.
Now that we have that out of the way… Let’s dive in.
1. CEO Fraud/Business Email Compromise
The first type of phishing we’ll discuss is known as CEO fraud. In a nutshell, CEO fraud occurs when a cybercriminal sends an email to a lower-level employee — typically someone who works in the accounting or finance department — while pretending to be the company’s CEO or another executive, manager, etc. The goal of these emails is often to get their victim to transfer funds to a fake account. Just a bit of bonus info for your upcoming trivia night: In the U.S., CEO fraud is often referred to as business email compromise (BEC), which the FBI says costs businesses billions of dollars.
For your viewing pleasure, I’ve included a real example of a CEO fraud email that I received from someone trying to be The SSL Store™’s CEO John Tuncer:
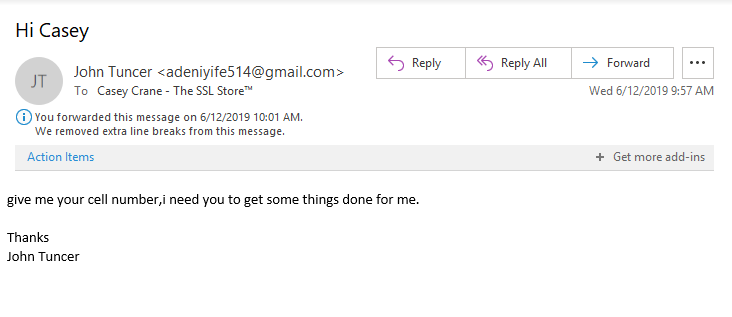
In this case, it was easy for me to tell that it wasn’t from him. For one, the email sender is listed as John Tuncer, but the email address isn’t his email account. Second, look at how the email is written — there is no space between the first section of the sentence and the second part. This is often the case when information is being copied and pasted. Additionally, typos are as common in emails as there are weeds in a field.
Third, at The SSL Store, we use email signing certificates to authenticate all of our employees. This email lacks any sort of digital signature or security measure. We’ll speak more about email signing certificates later in the article.
2. Clone phishing

The idea behind a clone phishing attack is to take advantage of legitimate messages that the victim may have already received and create a malicious version of it. The attack creates a virtual replica of a legitimate message — hence, the attack’s clever name — and sends the message from an email address that looks legitimate. Any links or attachments in the original email are swapped out for malicious ones.
The cybercriminal often uses the excuse that they’re re-sending the original message because of an issue with the previous email’s link or attachment to lure end-users into clicking on them. We wish we could say that this doesn’t work; unfortunately, though, it often does because it catches users unawares.
3. Domain spoofing
The next type of phishing we want to mention is known as domain spoofing. This method of attack uses either email or fraudulent websites. Domain spoofing occurs when a cybercriminal “spoofs” an organization or company’s domain to:
- make their emails look like they’re coming from the official domain, or
- make a fake website look like the real deal by adopting the real site’s design and using either a similar URL or Unicode characters that look like ASCII characters.
How’s that possible? In the case of an email-based attack, a cybercriminal forges a new email header that makes it appear like the email is originating from a company’s legitimate email address. In a website domain spoof, the cybercriminal creates a fraudulent website and with a domain that looks legitimate or is close to the original (apple.com vs apple.co, for example).
4. Evil Twin

While it sounds like it would be up the same alley as a clone phishing attack, an evil twin is actually a very different animal. Unlike the other methods of phishing we’ve mentioned in this article, an evil twin attack is a form of phishing that capitalizes on Wi-Fi. TechTarget.com describes an evil twin as “a rogue wireless access point that masquerades as a legitimate Wi-Fi access point so the attacker can gather personal or corporate information without the end-user’s knowledge.” This type of attack has also been referred to as the Starbucks scam because it often takes place in coffee shops.
Evil twin phishing involves a cybercriminal creating a Wi-Fi hotspot that looks like the real one — they’ll even use the set service identifier (SSID) that is the same as the real network. When end-users connect, the attacker can then eavesdrop on their network traffic and steal their account names, passwords, and view any attachments that the user accesses while connected to the compromised hotspot. (Tip: A VPN will keep your data secure even on a compromised Wi-Fi network.)
5. HTTPS phishing

We recently wrote about how URL-based attacks are on the rise. In fact, 58% of all phishing websites are now served via HTTPS. The approach cybercriminals use in these attacks is to send an email with only a legitimate-looking link in the email body. There’s often no other content except for the link itself (which may be clickable or a non-active link that requires the recipient to copy-and-paste the URL into their web address bar.
So why would anyone intentionally click on such an email? The short answer is because the attacker uses a variety of social engineering tactics to trick the email recipient into clicking on the link or copy-and-pasting the URL into their web browser (which makes this type of phishing email difficult for filters to detect). This includes sending the messages from an email address that appears legitimate — such as from the recipient’s boss, co-worker, or the CEO.
6. Smishing
SMS phishing, or “smishing,” is a form of phishing that capitalizes on the world’s addiction to text messaging and instant communications. Ever receive a text message from Chipotle? How about Ticketmaster? Smishing is a way for cybercriminals to lure users into downloading malicious payloads by sending text messages that appear to come from legitimate sources and contain malicious URLs for them to click on. It could be something disguised as a coupon code — 20% off your next burrito purchase — or it could be an offer to win free tickets to an upcoming show.
One way to avoid falling victim to smishing attacks is to refer to the U.S. Short Code Directory — yes, such a thing does exist — to see whether the message is being sent from a legitimate source. The best way to avoid it, however, is to not engage with any unsolicited text messages. If you didn’t sign up for text notifications, don’t click on the URL when you receive such a text. When in doubt about the authenticity of a message, simply rely on the lesson your parents and/or teachers taught you as a child: don’t talk to strangers.
7. Spear phishing
A spear phishing attack is a targeted form of phishing. Unlike general phishing emails, which use spam-like tactics to blast thousands of people in massive email campaigns, spear phishing emails target specific individuals within an organization. They use social engineering tactics to help tailor and personalize the emails to their intended victims. They may use email subject lines that would be topics of interest to the email recipients to trick them into opening the message and clicking on links or attachments.
Why is spear phishing so important? Because 91% of cyberattacks start with a spear phishing email. The goal is often to steal data or to install malware onto the recipient’s computer to gain access to their network and accounts. Unfortunately, traditional security methods may not stop these types of attacks because they are so highly customized that many traditional spam filters might miss them.
8. Vishing
You already read about smishing and understand that it’s phishing for SMS messaging. So, if you’ve guessed that “vishing” is “voice phishing” (phishing over the phone), then you’re be correct. A vishing attack occurs when a criminal calls your phone to try to get you to provide personal or financial information. They often use automated calls that re-route individuals who fall for their tactics and end up speaking with the criminals themselves. They also use mobile apps and other techniques to spoof their phone number or to hide their phone numbers entirely.
These attackers frequently use a variety of social engineering tactics to trick you into providing this information. They also are known to pretend to be someone else — the IRS, your bank, or an executive at your company who claims to work at another branch. They’ll claim that you owe taxes, or that your credit card has suspicious activity and needs to be shut down right away… they’ll first just need to “verify” your personal information before they can close the card and reissue a new one.
Don’t fall for these tactics.
9. Watering hole phishing
This lesser-known type of phishing attack is reminiscent of a scene from the animal kingdom. Picture a group of zebras, antelope, and other creatures on the Serengeti at a watering hole. To cool themselves, they edge nearer to the water and lean in to take a drink. One zebra decides to get a little cooler and wanders a little too far from the herd into the water. Suddenly, a crocodile bursts up from beneath the surface of the water and grabs them, dragging them under.
Yeah, you’ve guessed it: You’re the striped dinner in this scenario.
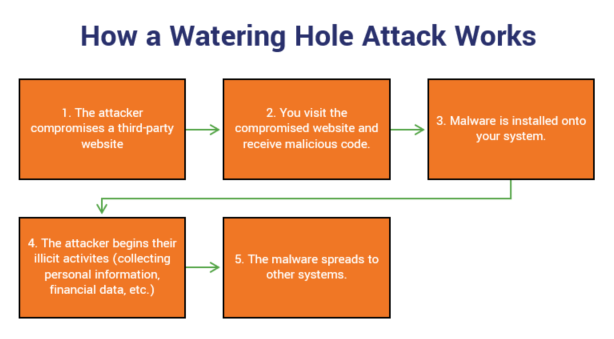
Watering hole phishing attacks target businesses by:
- identifying specific websites that your company or employees visit most often, and
- infecting one of the sites with malware.
The sites that are selected for infection might be a vendor whose services your company uses. The goal is to infect the websites so that when you or your employees visit, your computers will automatically be loaded with malware. This will provide the attackers with access to your network, servers, and sensitive information such as personal and financial data.
Will other people who visit the infect site fall victim to the attack? Sure. But they’re just collateral damage and extra victims for the cybercriminals.
10. Whaling

Whaling, a form of spear phishing, is a lot like the inverse version of CEO fraud. Instead of targeting lower-level individuals within an organization, the cybercriminal instead targets high-level executives such as CEOs, CFOs, and COOs. The goal is to trick the executive into revealing sensitive information and corporate data. These targets are carefully selected because of their access and authority within an organization. These attacks often use email and website spoofing.
Unlike general phishing emails, these messages rely on social engineering tactics using information they get from the internet and various social media platforms. They’re highly tailored to their audiences and often include:
- The victim’s name,
- Job title, and
- Basic details that make the communications look legitimate.
There are other types of phishing attacks — evil twin, snowshoeing— but we’d keep you here all day if we kept talking about all of them.
How you can avoid falling for many types of phishing attacks
Truly effective cybersecurity is a multi-layered approach. Here are some of the things you can do to help prevent your business from becoming the next phishing-related headline:
Train your employees to adopt email best practices
This should go without saying, but it bears repeating since this still seems to be a sticking point for some businesses: train your employees. All of them. This includes everyone from the janitors to the CEO.
Train your employees to adopt email best practices
This should go without saying, but it bears repeating since this still seems to be a sticking point for some businesses: train your employees. All of them. This includes everyone from the janitors to the CEO.
Implement the use of email signing certificates
As I mentioned earlier for the CEO fraud section, we use email signing certificates here at the SSL Store™. These digital security certificates are known as S/MIME certificates because they use secure/multipurpose internet mail extensions to encrypt the content of our emails (and any attachments) and to digitally sign our communications.
Don’t Get Phished.
Email is the most commonly exploited attack vector, costing organizations millions annually. And for SMBs, the damage can be fatal in terms of suffering data breaches & going out of business. Don’t be another statistic.
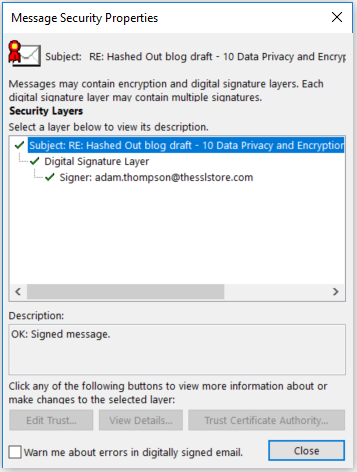
Below is an example of an email that my boss sent to me using his email signing certificate:

Below the “From” and “To” fields, it says the email is “Signed By” and lists Adam’s email address. To the right, you’ll notice a small ribbon icon. When you hover over the graphic, it displays a message that says “Digital Signature is trusted. Click here for details.” When you click, it displays the following notification:
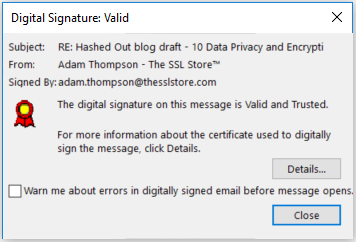
When you click on “Details,” it breaks down the encryption and digital signature security layers for additional information.
Other tips for preventing many types of phishing attacks include:
- Using a password manager — A trusted password manager enables your employees to have and use complex and secure passwords for every account without the hassle of having to remember all of them.
- Turn on two-factor authentication (2FA) — This protective measure requires multiple pieces of information for someone to be able to log in. It requires two of the following:
- Something you know (a password, passphrase, etc.);
- Something you have (a mobile app, a smart card, a personal token, etc.); and/or
- Something you are (biometrics such as a retinal scan, fingerprint, etc.).
- Using a sender policy framework (SPF) — This is a type of email validation system that allows domain managers to authorize specific hosts to use a domain.
- Verifying suspicious communications through official channels — If you receive a phone call from someone claiming to be your bank, hang up and call your bank directly using the phone number on the back of your card. If you receive an email from someone claiming to be the CEO who wants you to transfer money, send sensitive data or anything else even remotely suspicious, call them or their assistant on an official company phone line. Don’t ever rely on the contact information provided in a suspicious communication.
- Using websites that are secure and encrypted — Ensure that your website — and those that you visit — are secure and encrypted. This means visiting websites that use secure protocols (HTTPS) instead of insecure ones (HTTP). You can secure your website using SSL/TLS certificates, which protect the data that is transmitted between your site and your end-users’ web browsers.




