Ready to learn Marketing & Customer Analytics Training? Browse courses like Increase Cross Selling and Upselling of Products and Services developed by industry thought leaders and Experfy in Harvard Innovation Lab.
The demise of end-user created profiles and the rise of a trusted digital identity.
In an era of consumerization of IT, mobile users demand a new way of interaction and organizations may finally have to face the reality that user created profiles are unreliable and they must embrace new methods of authentication that balance security requirements and user experience, opening the path to the use of trusted digital identities.
The latest article from the Wall Street Journal on how banks are looking to address their identity fraud problems highlights one of the issues that fin-tech is facing, but is one that cuts across any organization trying to expand their services to an ever growing mobile user community.
The creation of fake profiles is not a problem limited to social media platforms, but is an on going problem for every organization. One that is exacerbated by the ability to create user profiles based on the large amount of data and the easy access to personal information due to the quantity of user information that is available from the multiple data breaches, data brokers, phishing techniques, etc., making the ability to trust a user created profile almost impossible.
The problem is — how can an organization verify that they are interacting with the proper end user ? and how can the user gain access to services without going through an excruciating amount of pain to create a complex profile and password that they will promptly forget after the initial interaction.
Bridging both requirements is the role that trusted digital identities can provide.
So what is a Trusted Digital Identity — one of the best descriptions is from Tim Bouma in his presentation at the FDW50 Event — “ It is an electronic equivalent of who you are as a real person, used exclusively by you, to receive valued services and to carry out transactions with trust and confidence”.
How do we achieve nirvana ? There is a lot of work being done at a global level, by many government and organizations trying to address this problem. The problem, is time and willingness — all of the approaches require the breakdown of identity silos, governance and agreements on processes that currently inhibit innovation. The idea of slow change is driven by the fallacy that user profiles are still useful and costly to change, instead of focusing on the value that can be extracted by managing identities in a new holistic way.
A Sample Use Case — Mobile Medical Wallet
The following use case is an approach that is being tested and developed by Anthrosight Solutions. Their product is an independent and mobile medical wallet- aggregating information from multiple Electronic Medical Portals, Sensors and other data sources to allow the secure sharing of such information for rapid consumption by medical professionals and others.
Based on their objective, the need to have a clear understanding of whom the user is before accessing information, is imperative; as their value, is delivering validated information to the proper parties, all based on user consent.
So, going back to the identity questions and why is this important — For a user to gain access to their medical records it is critical to verify their identity; not only for security purposes but to ensure that the use of such identity for accessing, sharing or creating new information is performed by/for the right individual, a concern reflected in the following study by the Joint Commission — “Quick Safety 45: People, processes, health IT and accurate patient identification” .
The image below is a graphical representation of the approach. An approach that relies on remote identity verification to onboard customers; using trusted external service for verification and based on the results, creating a digital identity that can be then utilized to authenticate and gain access to external services.
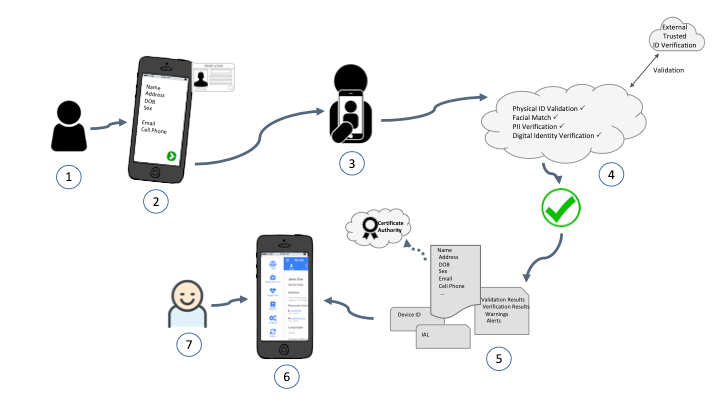
User on-boarding via remote identity validation
The following is a description of each step:
- End user goes to the registration page — downloads the application
- They take a picture of their physical identity document
- They take a selfie within a specific time
- AI tools provide a method to validate the document, perform a biometric check between the physical ID and the selfie picture. Once that is verified, then additional information checks are performed against trusted sources, like the document issuing organization, service bureaus, etc..
- Once the information has been verified, it generates a digital identity that represents that individual — The information is bound to the individual and its device, lastly it may also be shared with a central authority for an additional layer of security, verification and management.
- Access is granted to the application and the users medical information
- The whole transaction generates a pleasant user experience, as in less than 15 seconds, a user is able to onboard and gain access to their medical record. In comparison, it takes over a minute for the user to create their profile, enter information, create a user name, complex password and secret question manually.
Is this new ? Progress is made one step at a time and while identity verification is being performed with a greater extend in the fin-tech space, it is always after the customer has created their user profile during the on-boarding process.
The change is turning the process around, and use the validation and verification process right up front, bypassing the need for the user to create a profile or perform manual entry. Leveraging the on-boarding process to create a single verified digital identity that can be used for many other activities and parties.
The approach, opens up the opportunity to then link the digital identity to new authentication protocols (like the ones created by FIDO Alliance) and avoid the need to create passwords or share secrets.
This is a simple approach, that leverages current processes to achieve an objective. Using a current verified identity and creating a derived digital identity that identifies the user and allows them to gain access to services without passwords, delivering a balance between the user experience and the requirements of the application or service providers.
A much more extensive description can be found in Tim Bouma . “Digital Identity in Canada” presentation, delivered at the FWD50 event on November 7,2018 . He expands on the possibilities, use cases and the impact of using trusted digital identities for many types of transactions — describing a path to deliver on the promise of a single trusted identity to gain access to all kinds of services. Reducing end user friction, enhancing security, reducing cost, fraud and driving innovation.
There is plenty of research, reports, and conversations regarding the value of digital identities. The issue is not a lack of understanding but a willingness to change. The underlying infrastructure is in place, but unless organizations take the first steps and address the issue head on, the data breaches, end user frustration, identity /transactional fraud and other security issues will continue to grow and hamper the ability for innovation and progress.
In summary, here is a link to a timely post by Andrew Nash, describing the important role identity will play in the new economy and why identity verification and strong authentication are no longer and afterthought but are at the forefront of innovation — identity is the steam engine driving the digital economy.
Data may be the new oil, but identity will drive the new economy and future innovation, maybe it is time for organizations to embrace such change and let the past finally rest in peace.




