In Part 1 of this miniseries, I described the base level of my personal cybersecurity setup. In Part 2, we talked about virtual private networks (VPNs), including the fact that they still leave you exposed when you are connecting to the internet via a Wi-Fi network, even if you are in your office or at home. As part of this, we also considered the rather cunning technology from the folks at WifiWall.
In this column, I’d like to present a couple of interesting cybersecurity technologies that recently caught my eye, but first I’d like to give a shout-out to the National Westminster Bank, commonly known as NatWest, in the UK.
Online Banking
I currently hang my hat in the USA. We like to think that we are at the forefront of technology over here. In reality, however, we are sadly lacking in some respects. Take credit and debit cards that are equipped with embedded microchips along with the traditional magnetic stripes. These chips provide added security when making transactions at stores or ATMs. It’s no exaggeration to say that the folks in the UK and other parts of the world had these chips in their cards years before we finally got them in the USA. How can this be? I have no idea.
I use two banks here in the USA, one for personal stuff and one for business transactions. I also maintain my old NatWest bank account in the UK. This is partly for nostalgic reasons (I’ve had it for almost 60 years since I was 5 years old when my parents took me to the branch at the bottom of the road and opened a savings account in my name), and partly because it’s sometimes handy to have a local account with a local debit card when I’m over visiting my dear old mom.
I remember the days when I wouldn’t dream of using online banking because of security concerns, but it really is so beguilingly convenient, especially these days if you are under a lock-down or “shelter-in-place” order. When I send an invoice to one of my clients, they simply wire the money to my business account, from whence I can distribute it as I wish.
One thing I’ve noticed is that, despite all of the questions and passwords and whatnot, the USA banks fall far short on the security front as compared to UK banks like the NatWest. Take a look at the picture above. This is a little security gizmo the folks at the NatWest sent me for free. If I wish to transfer money to or from my NatWest account, after going through multiple layers of passwords and special pin numbers and suchlike, their system will ask me to insert one of my bank cards into this gizmo. They will then generate a special code number for me to enter into the gizmo. In turn, this generates a new code that I enter into the browser to prove that it is indeed yours truly who wishes to make the transaction. All I’m saying is that I feel much more confident about the security at the NatWest in the UK than I do with either of my banks in the USA, which is a pretty sad state of affairs when you come to think about it.
The Fabulous Firewalla
With regard to the WifiWall technology discussed in my previous column, the computer I’m penning this column on is currently using the WiFi network in my home. Knowing that my WifiWall Traveler is constantly monitoring all of my WiFi traffic, poised to leap into action if it sees anything untoward, gives me a high level of confidence that all is as it should be.
But what if someone manages to penetrate my network via some other means, infiltrating some malware into my system, for example? Well, I was just introduced to a product called a Firewalla. This is a smart firewall device that you simply plug into your router, after which it monitors your network traffic. If any of your devices unexpectedly start exfiltrating (uploading) data to the outside world, your Firewalla alerts you via an app running on your smartphone, including information as to with whom the data is being shared and in what country they are located. I believe that there’s also an option for the Firewalla to shut the problem device down if you wish. Firewalla will also block hackers and cyberthieves from being able to breach your smart home devices to steal your person information.
There are currently two flavors of this little beauty — the affordable Firewalla Red is suitable for networks running at 100 megabits-per-second (Mbps) or less, while the more powerful Firewalla Blue addresses networks up to 500 Mbps. Furthermore, a multigigabit Firewalla Gold is scheduled for release sometime around summer 2020.
The guys and gals at Firewalla were kind enough to send me a Firewalla Blue to play with. The photo below shows the device just after I’d taken it out of the package. In addition to the Firewalla itself, there’s also an Ethernet cable to connect it to your router and a USB cable with associated adapter to power the little scamp.

Now, to be honest, the way I’d originally envisioned this device working is that it would go in-line between the modem and the router. Had this been the case, it would have been a problem for me because my internet provider has installed an all-in-one modem and Wi-Fi router. Happily, the Firewalla simply connects into one of the Ethernet ports on the router as illustrated below.
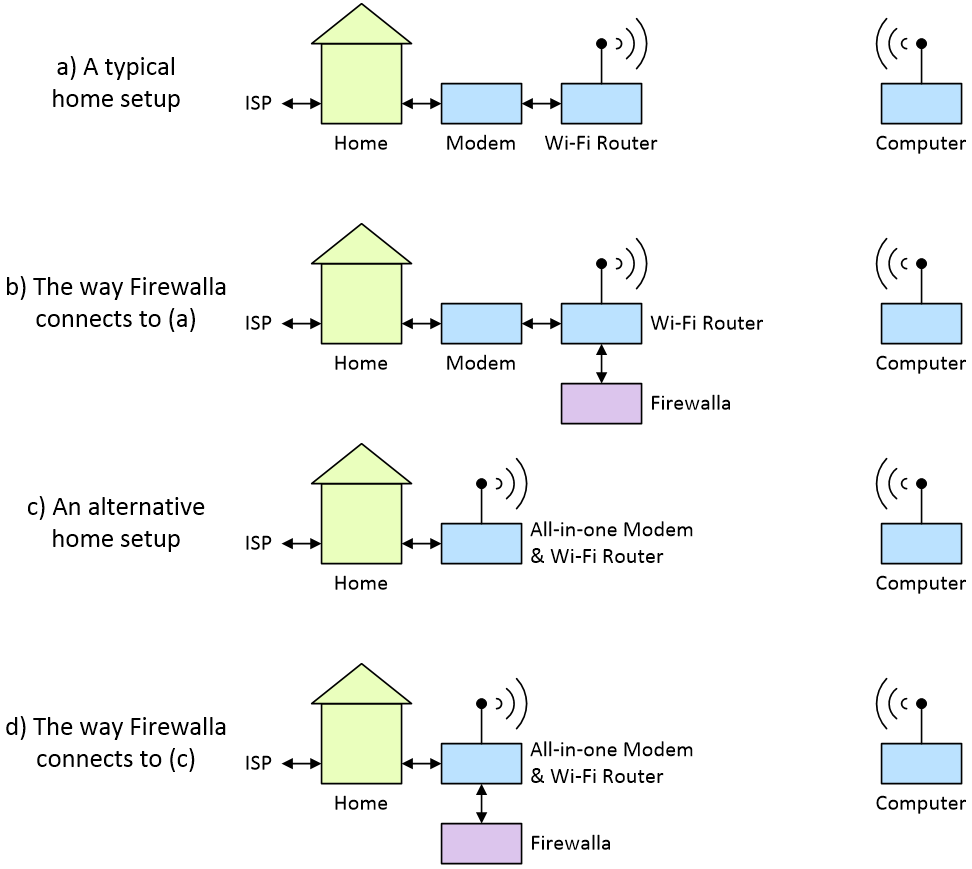
Unfortunately, this is where I ran into a bit of a “gotcha.” Everything started off swimmingly at first. I downloaded the free app to my smartphone, connected the Firewalla to my router, and followed the incredibly easy setup process, all the way through to the point where the Firewalla informed me that my router wasn’t compatible with the “Simple Mode.”
If my router had been up to the task, then my job would have been done at this point, without my having to make any modifications to my network whatsoever. However, since my router wasn’t compatible, the Firewalla gave me an option of using something called DHCP Mode. This sounded easy enough but… both my wife (Gina the Gorgeous) and I are currently working from home because of the shelter-in-place order, while my son — who lives at home with us — is completing his university degree online.
The bottom line was that I didn’t want to do anything to mess up my network, so I decided to stand down until I can get my ISP to install a better router. Speaking of which, if you are tempted by this technology yourself, here’s a handy-dandy list of supported routers.
I’d like to close this topic by saying that I was tremendously impressed with how smooth the installation process was, right up to the point when the Firewalla discovered my router was sub-par, and I can’t wait to add this device to my home security arsenal as soon as I manage to upgrade my router.
The End of Ransomware?
As I mentioned in Part 1: “One thing I worry about is my machine becoming infected by ransomware. In this case, a malicious application encrypts all of the data files on your system, after which the nefarious perpetrator tries to extort money from you (typically in the form of an untraceable cybercurrency like Bitcoin) with the promise of decrypting them again.”
Well, I was just chatting to the folks at Active Cypher. These chaps and chappesses have an incredibly sophisticated security solution called Active Cypher File Fortress (ACFF). This provides artificial intelligence (AI)-driven threat protection and incident response that prevents the spread of breaches inside any data center and cloud. The only problem with ACFF from my point of view is that it’s a cloud-based solution targeted at companies, corporations, and enterprises with IT departments who can install and manage everything.
But wait, there’s more, because the folks at Active Cypher have just announced a new product called Ransom Data Guard that will be applicable to both corporate and individual users.

Ransom Data Guard utilizes a combination of Active Cypher’s proprietary encryption orchestration, smart AI, and advanced endpoint protection. The guys and gals at Active Cypher say the result is to shield users from all permutations of ransomware attacks like WannaCry, RobbinHood, TeslaCrypt, Locky, Petya, Hidden Tear, Bad Rabbit, Gandcrab, Rakhni, Sodinokibi, and Rannoh.
Of particular interest to someone like me is that Ransom Data Guard provides immediate protection without any user interaction. Now, that’s what I’m talking about!
A lot of this is about confidence. When I’m outside working in the yard and I see the green LED on my natural gas-powered emergency generator bidding me a cheery “Hello,” it gives me a warm feeling to know that if we lose power to the house during a storm, for example, then we are still covered power-wise. Similarly, knowing that an AI was running on my computer providing 24/7 detection and protection from ransomware would give me a high level of confidence and make me a much happier man.
I was just visiting Active Cypher’s website. It seems this technology isn’t available for purchase just yet, but there is a form to request early access. I just subscribed. I will report back further when I bolster my personal cybersecurity system with this bodacious beauty. Until then, as always, I welcome your comments, questions, and suggestions.




Like!! Really appreciate you sharing this blog post.Really thank you! Keep writing.
Thank you. For more updates, please subscribe to our blog
Thank you. For more updates, please subscribe to our blog