The issue of Internet of Things device security is one of the main growing pains that inevitably follow the industry which is expanding at a rapid pace. As Statista indicates, by 2025 there will be 75 bln connected devices that we will have to protect against virtual and physical attacks.
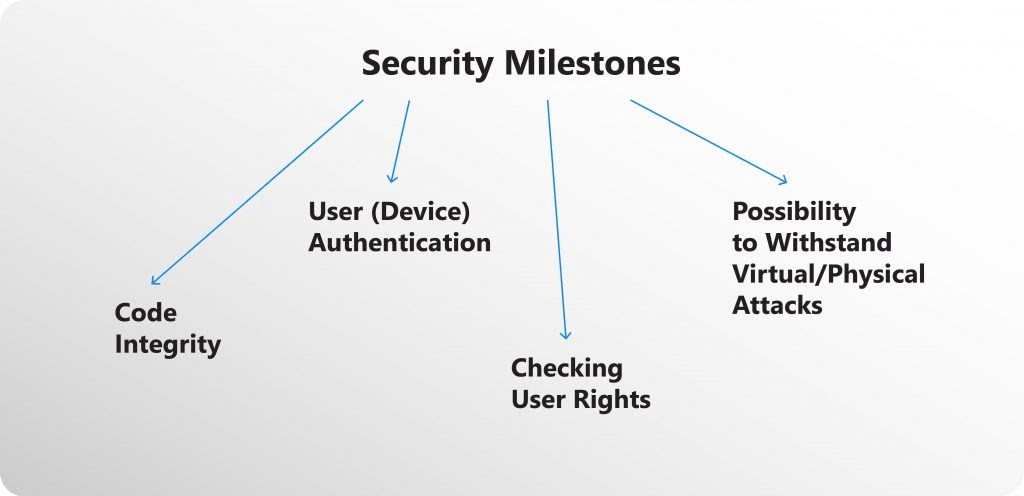
One of the main security indicators of IoT devices is the ability to personalize a device without additional effort and expense (connect it to the network and enter access keys). In addition, code integrity and the ability to withstand attacks are important. Problems arise both on the part of users and manufacturers. For example, not all device owners replace factory passwords with more complex ones. Manufacturers, in the pursuit of quick money and the desire to quickly bring the device to the market, do not always properly test their product codes.
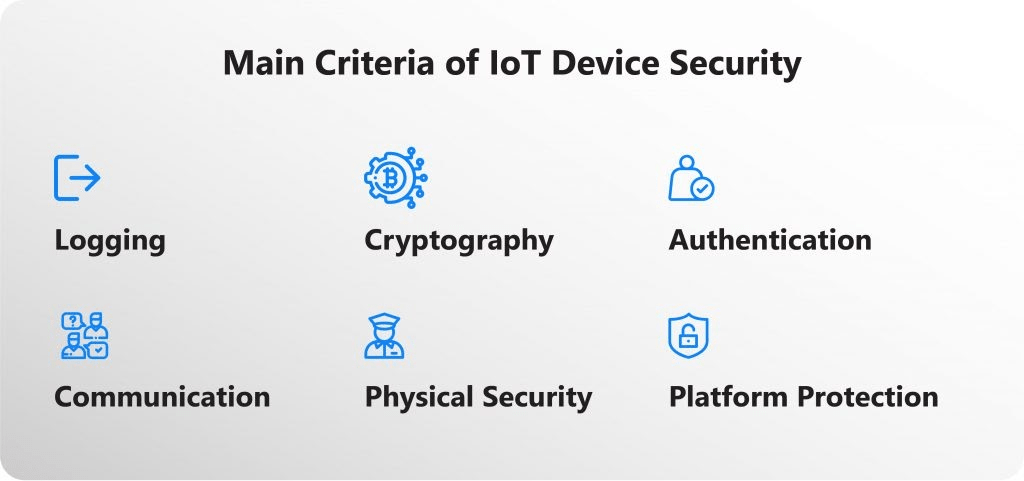
More on Internet of Things weak spots was covered in our previous article. As we noted there, the main issue with the Internet of Things is that there are no uniform security standards, which is an inevitable consequence of the broad variety of devices on the market. Sometimes you have to save on something in order to be competitive in comparison with others. And, as you may guess, the functionality often falls victim in this struggle, since you have to fill the available IoT memory with as much as possible sacrificing some lesser evil.
How to Secure IoT Devices
Botnets are a common tool which hackers use in carrying out their attacks. One of the most vivid occurrences took place in 2016 when as a result of a DDoS attack the Mirai botnet brought down most popular American websites. The malware cracked combinations of default logins and passwords and hacked thousands of IoT devices. What is more, intruders uploaded the source code on the Internet, which increased the risk of it being used by other hackers. Below is a typical architecture of a DDoS attack.
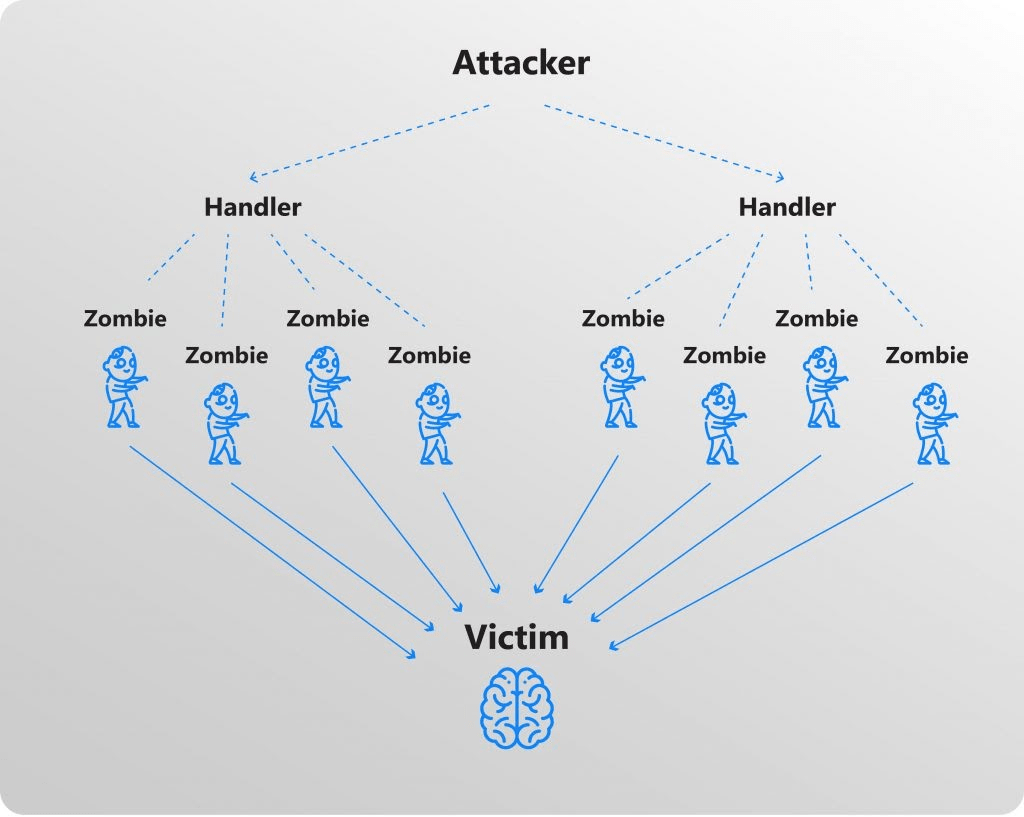
These and similar attacks can bring physical harm to people (e. g. if hackers have got access to explosive and fire-hazardous equipment) or cause delays or downtime at production sites (which in turn leads to sufficient losses). In addition, by hacking one smart device, malicious users can get access to the entire network, including entrance locks and bank accounts.
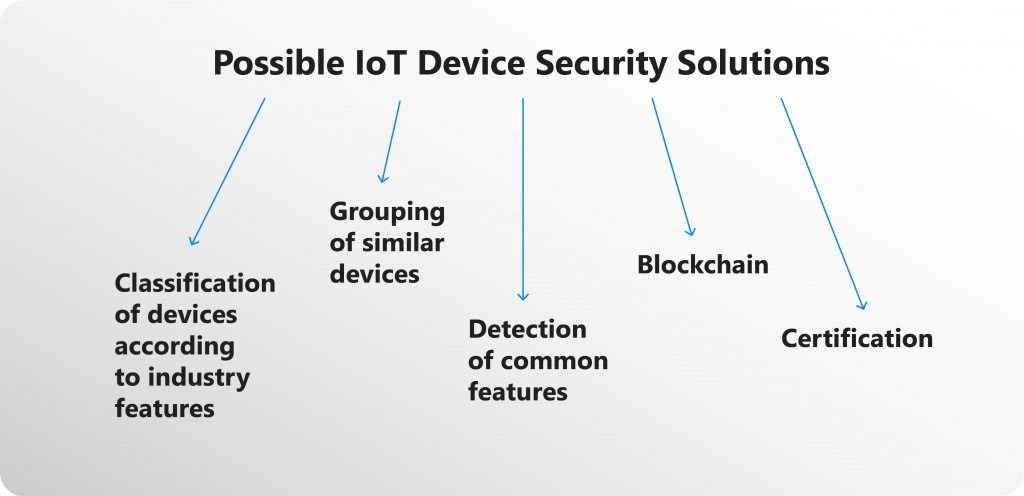
Some of these solutions were covered in our previous article. Let’s focus on certification this time.
Can certification be the best way to secure IoT devices?
The issue associated with the security of IoT devices can be partially resolved by certification. Passing tests and obtaining appropriate certificates will provide clients with some protection against attacks by cybercriminals. The main condition for such a procedure is that it is available to all manufacturers and does not turn into a pure formality.

Online Trust Alliance (OTA) came up with an idea of how to secure your IoT devices. The company compiled a list of requirements for manufacturers and service providers — IoT Trust Framework. This list should ensure the safety and viability of IoT products. Based on it, you can design certification programs for devices, as well as assess existing risks.
A certain number of IoT certificates, which were developed by private companies, are already in use. For example, Verizon – ICSA Labs created its own program that inspects the security of IoT devices.
The solution developed by UL Cybersecurity Assurance (CAP) tests not only product safety, but entire systems as well. A CAP certificate confirms that software updates for a device will not reduce security or increase the risk of attacks.
In 2018, the German software developer SAP introduced its IoT device certification program in the CIS. Within its framework, devices are tested and receive a respective quality mark, which confirms that the devices are safe and can be used in IoT projects.
The European Commissioner for Digital Economics and Society, Thibaut Kleiner, believes that measures to protect the IoT from cyberattacks should be taken at the state level, in particular, to make certification mandatory for all devices of the Internet of Things. Such a procedure should apply not only to devices, but to networks and cloud storages as well.
What can you do to secure your IoT devices?
If you want to secure your Internet of Things infrastructure, you’ll have to possess a carefully crafted security strategy. According to this strategy, it is necessary to protect data in the cloud, to ensure data integrity during data transfer over a public network and to thoroughly prepare devices for further use. Each next level provides better security guarantees throughout the entire infrastructure.
This carefully thought-out security strategy can be developed and implemented with the active participation of various parties involved in the design, development and deployment of IoT devices and infrastructure. Let’s consider what each of them can do to ensure the success of your IoT project.
- Manufacturer or integrator of IoT devices
As a rule, these are manufacturers of deployable IoT devices, equipment integrators who assemble equipment originated from various manufacturers, or equipment suppliers who provide IoT deployment equipment manufactured or integrated by other vendors.
- IoT solution developer
An IoT solution is usually developed by a software developer with a good share of expertise in this field. This developer may be part of a team within the company or a system integrator specializing in this sphere. An IoT solution developer can design various IoT solution components from scratch, integrate various box or open source components, and implement solution accelerators by introducting slight modifications to them.
- IoT solution deployment specialist
The developed IoT solution should be deployed in a runtime environment. At this stage, equipment is deployed, device interaction is established, and solutions are deployed on hardware devices or in the cloud.
- IoT solution operator
Once deployed, the IoT solution requires long-term monitoring, updates, and maintenance. These tasks can be performed by a team within the company, which includes information technology specialists, equipment operation and maintenance teams, as well as specialists in a specific area who monitor the work of the entire IoT infrastructure.
Below we provide a quick overview of developing, deploying, and operating a secure IoT infrastructure for each of these process participants.

What measure should be taken to secure IoT devices?
Manufacturer or integrator of IoT devices
- Ensure the compliance with the minimum requirements for equipment
- Protect the IoT equipment against unlawful modifications and alterations
- Create the solution on the basis of secure equipment
- Ensure that updates are safe and secure
IoT solution developer
- Choose the safe way to develop software
- Pay special attention when selecting open-source software
- Be cautious when integrating
IoT solution deployment specialist
- It’s obvious but deploy the solution securely
- Ensure the security of authentication keys
IoT solution operator
- Ensure timely updates of your system
- Take care to protect yourself against malicious activity
- Frequent audit is a must
- Ensure the physical protection of the IoT infrastructure
- Protect your cloud credentials
We will cover the above best practices in our upcoming article. Stay up-to-date!




